Inside the war game that lets companies play out a cyber attack
But it comes with a harsh lesson: the hackers usually win.
A NEW SITUATION room-style simulation gives Irish companies the chance to see firsthand how to manage a cyber attack.
The initiative, developed by PwC and dubbed Game of Threats, is modelled on a war-game scenario. The turn-based simulation demonstrates what a cyber attack looks like and the different problems a company is faced with during the fallout of a system breach.
The point of the game, which Fora sat through today, is to give companies a better perspective of the damage cyber attacks can do and to highlight what infrastructure could be put in place to fend off future attacks.
Each game, however, contains a harsh lesson for companies: the hackers usually win.
Hackers have shown their power in recent years through a series of high profile incidents that hit big US corporations.
In 2014, Home Depot revealed that hackers gained access to its database and stole the details for 56 million credit and debit cards, while Sony Pictures suffered a huge malware attack that took its system offline.
PwC Ireland cyber security lead partner Pat Moran said it is more important than ever for companies to understand the ramifications of a cyber attack.
“The issue has evolved far beyond data loss. Beyond financial and reputational damages, we are seeing impacts to competitiveness, product and service quality and customer retention.”
How the game works

Pick a side – Teams play as the generic Acme Corporation or can take on the role of a hacker to get a better appreciation of the tools at their disposal. There are 12 rounds and each team has 60 seconds to take its turn.

Playing cards – Both teams get a set of playing cards. Each card has a specific action and can be played by spending resources. For example, a company can use a card to scan for specific cyber attacks affecting the company, while hackers could use a card that send emails to a company in the game containing malware.
Other cards can be used to counter moves made by the opposition. For instance, after receiving a lot of emails laced with malware, a company could restart its entire computer network to negate the damage done.

Situation room – Each team has its own screen and device that can be used to make decisions on the best way to win the game. An overview of what’s going on is also on display to both teams.

Team screens – The private screens of both teams show the moves available to them during each turn, the resources left to spend and the infrastructure in place to protect or attack a company – for example, an incident response team or breach specialist.
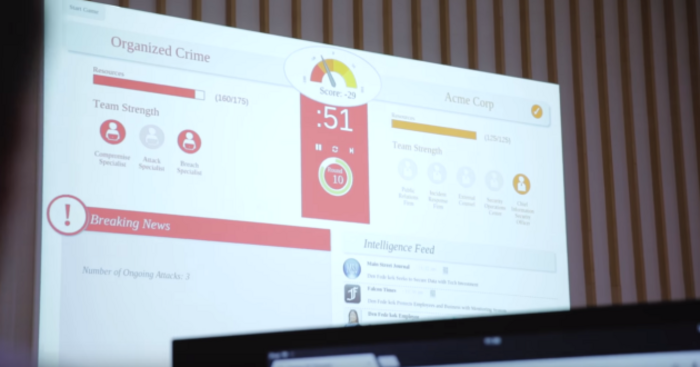
Monitoring attacks – The overview screen is the only way to identify what attacks are ongoing. Teams playing as the company can monitor any cyber attacks under way by checking an intelligence feed that is populated with either customers complaining that the company’s website is down or media outlets reporting on an attack.

Winners and losers – The game can be won or lost in two different ways. Basically, if the dial is closer to 9 o’clock after 12 rounds, the hackers win for causing more disruption than the company could cope with. If the dial is closest to 3 o’clock, the company wins for fending off the cyber attack.
However, if the dial goes past either threshold before the 12 rounds are complete, the dominant team wins by total knockout.
Ransomware threat
PwC cyber security consultant Daniel Muldoon said the game has proven popular with companies in the financial sector and he expected to eventually work with companies across all major industries.
“Cyber attackers don’t discriminate. I don’t think there is an industry that won’t be affected by a cyber attack. I think any industry will find value from conducting this kind of exercise.”
In Ireland, ransomware is many hackers’ weapon of choice. Using this method, hackers hold company data hostage until a fee is paid for its release.
PwC Ireland cyber security director Leonard McAuliffe said that the best way for a company to cover its back against a ransomware attack is to constantly backup all of its data.
He said if a company has a regular back up of its databases, hackers cannot hold the company to ransom for that information.